Workflow
Flow of the Extension
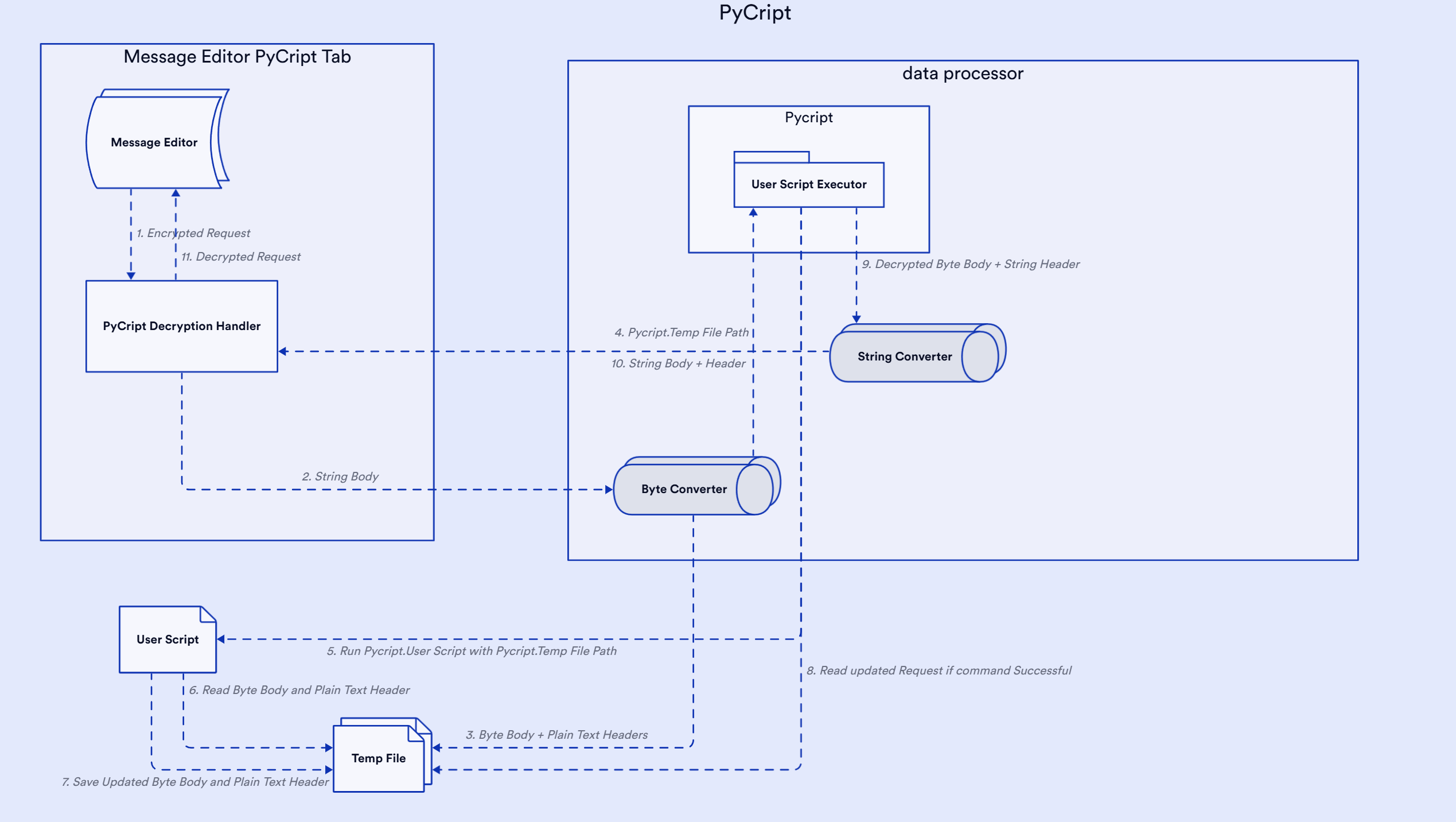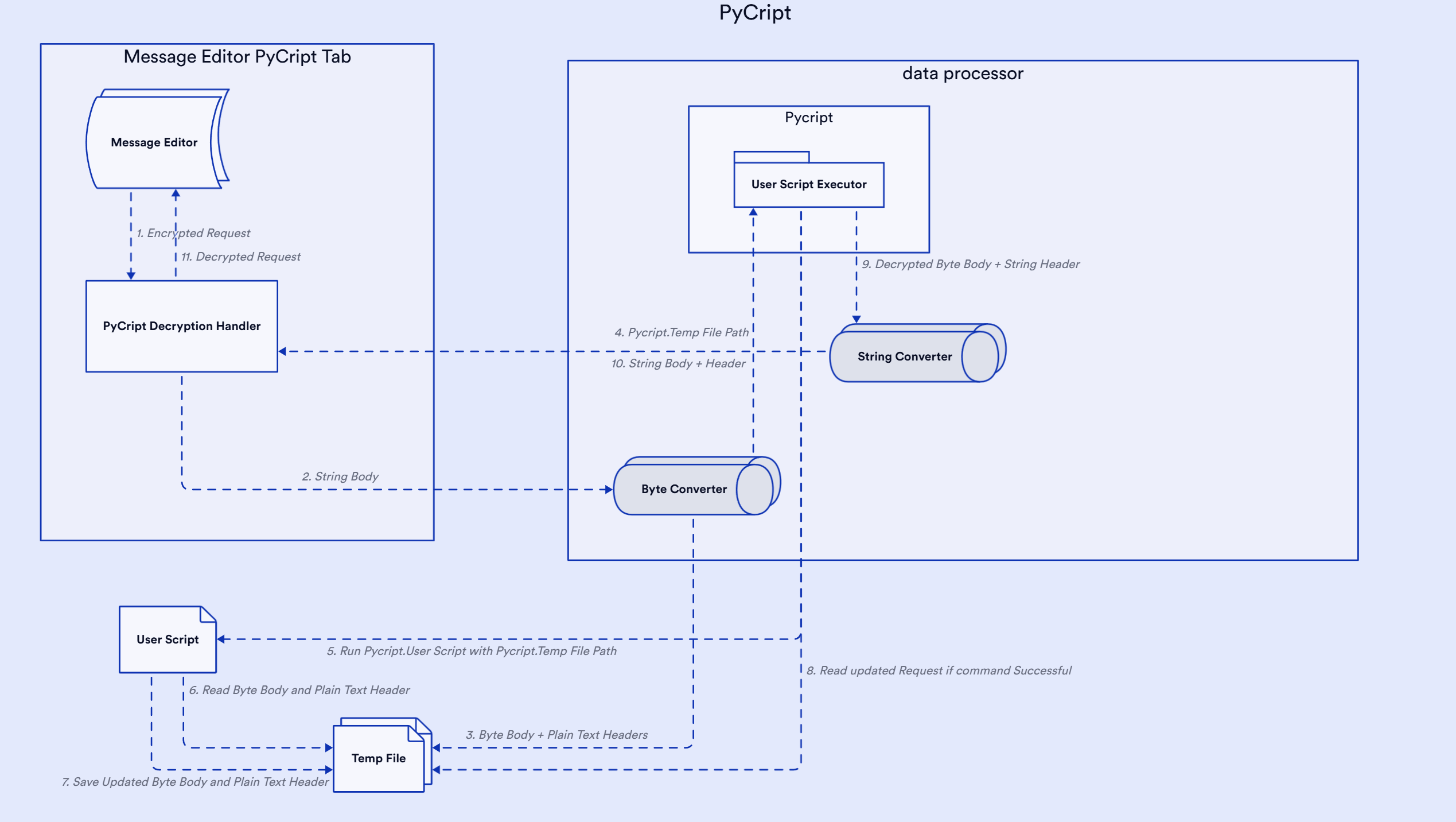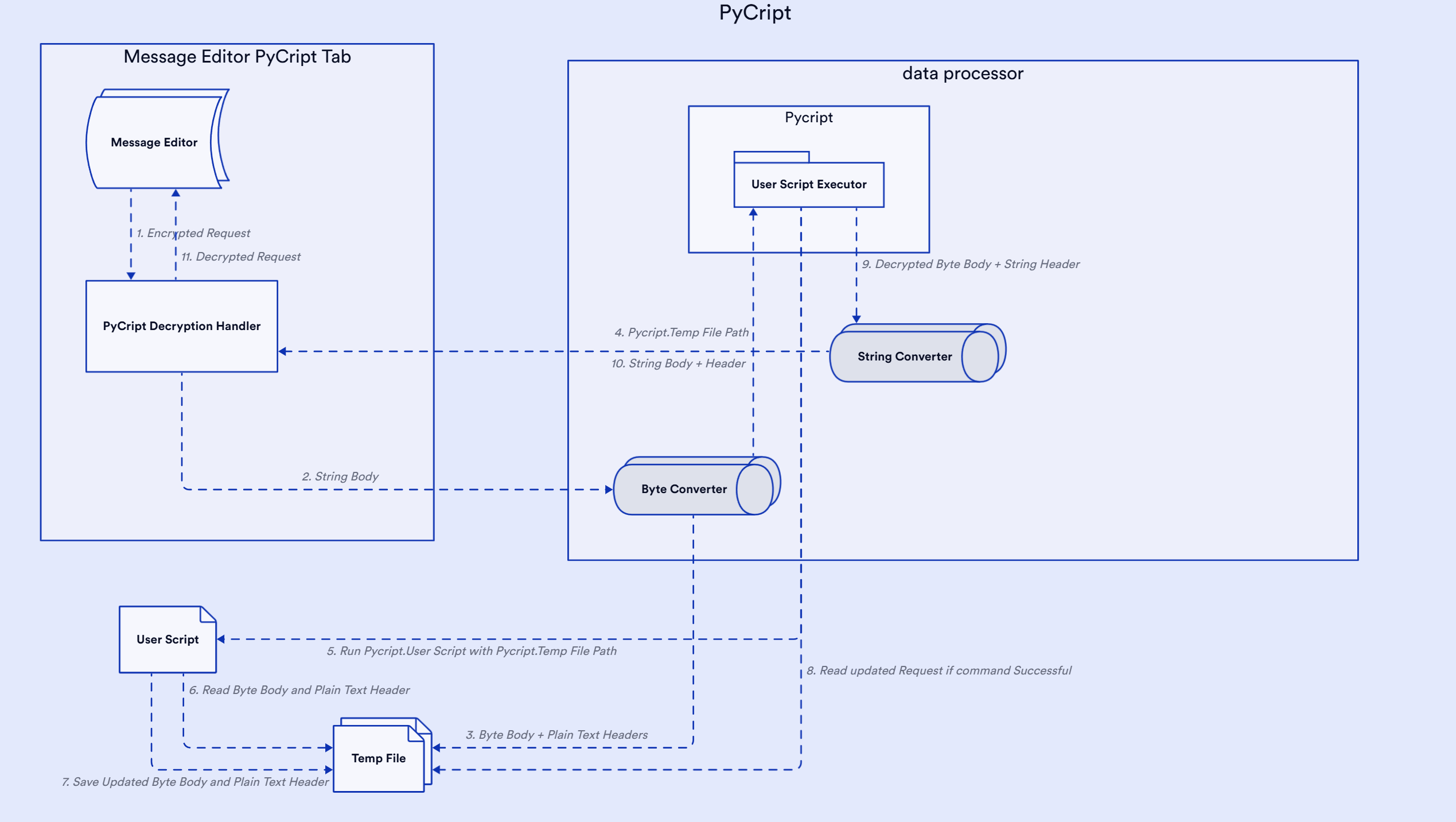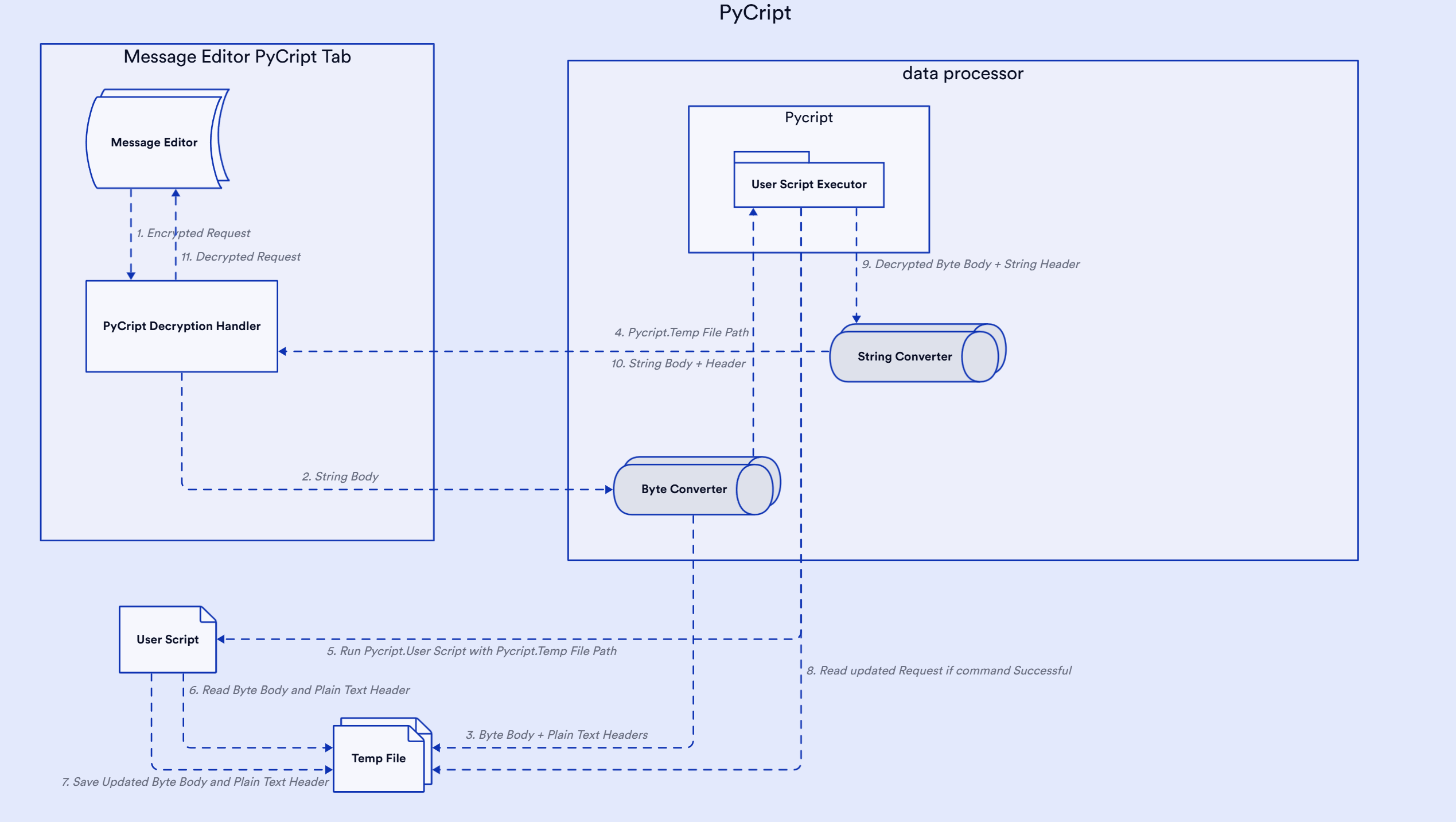
PyCript utilizes system commands to run user-specified encryption and decryption scripts. The extension passes the HTTP request/response body or parameters as raw data (text or binary) and headers as plain text, storing them in a temporary file. The file separates headers and body/parameters using the marker \n--BODY_END--\n. PyCript executes the system command with the path to the temporary file provided to the user script. After execution, the extension reads the updated request or response data from the same temporary file, using the updated body/parameters and headers directly. These updated values are then replaced in the request or response within Burp Suite.
Commands
The PyCript extension generates a temp file and stores the request body/parameter and header in raw format. The extension passes the temp file location to the encryption-decryption script using -d command line argument.
- node script.js -d tempfile-path
- python script.py -d tempfile-path
- java -jar script.jar -d tempfile-path
The temp file will have encrypted/decrypted parameter or request body and request header in the following format:
{"username":"admin","password":"admin"}
--BODY_END--
POST /decrypt HTTP/1.1
Host: localhost:8000
Content-Length: 48
sec-ch-ua-platform: "Windows"
Accept-Language: en-US,en;q=0.9
For binary encrypted data, the body before the marker will contain raw binary bytes:
��V�6��K� �����[Q}�18'tt�|^KAF�� 섐���j~.H�
--BODY_END--
POST /decrypt HTTP/1.1
Host: localhost:8000
Content-Length: 48
Note
Headers are only available for request encryption/decryption, not for response.
Note
Headers can only be edited if Request Type is Complete Body.
Note
In case of response encryption/decryption, the temp file will have no data after --BODY_END-- as no headers are present for response.
Note
Your script should read the file as binary to properly handle both text and binary encrypted data. Write output in the same format: data + \n--BODY_END--\n + headers.
Note
WebSocket messages do not have headers, similar to responses. The temp file will have no data after --BODY_END-- but the marker must still be included in the output.
- Complete Body - The extension will take the request/response body as raw data, take plaintext headers, and save the file in the above format.
- Parameter Value - PyCript is designed to iterate through the request/response parameter values, take raw plaintext headers, and save the file in the above format. It will then update each value one by one.
- Parameter key and value - The PyCript extension adopts a similar approach to that of parameter value. It iterates through each parameter name and value, passing them one by one to the script for updating.
Usage
- Start by loading the PyCript extension into Burp Suite.
- Choose the language you want to use for encryption and decryption. (See Select Language for more details)
- Load the encryption and decryption file.
- Decide whether you want to apply encryption and decryption to the request, response, or both, and select the appropriate type.
- For request encryption and decryption, specify the method you want to use (GET, BODY, or Both).
- Select the Request or Response Type like Complete Body, Paramter Value etc.
- Make sure the URL you want to work with is within the scope of Burp Suite.
- Once you've located the encrypted request or response, a new PyCript tab will be generated next to it, with a plaintext version that you can edit as needed.
Parameters
It is important to verify the supported request parameters or content types by PyCript. The following methods encompass the content types and parameters supported by PyCript:
The PyCript extension leverages the APIs offered by Burp Suite to examine get and body parameters. However, there may be situations where its performance is suboptimal when faced with encrypted or encoded parameters containing multiple = characters. If you encounter challenges in parsing such requests, it is recommended to use the complete body options and incorporate customized parsing into your script.
POST /crypto/myprofile?username=KtKB81Oamvuzo9entPFKZQ%3d%3d&password=KtKB81Oamvuzo9entPFKZQ%3d%3d HTTP/1.1
Host: localhost:8000
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.134 Safari/537.36
Connection: close
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
Content-Length: 24
username=KtKB81Oamvuzo9entPFKZQ%3d%3d&password=KtKB81Oamvuzo9entPFKZQ%3d%3d
PyCript has included JSON support since its initial release. The extension utilizes custom parsing methods to handle JSON objects, as Burp Suite itself does not natively support direct manipulation of JSON objects. Starting from version 0.2, PyCript extends its support to handle nested and complex JSON objects.
POST /crypto/login/ HTTP/1.1
Host: localhost:8000
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.134 Safari/537.36
Connection: close
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
Content-Length: 77
{"username":"HgE40uCnUDbOfuat6om5QA==","password":"FZbf3I/h9ORUV+H6Wzv4gA=="}
Info
The version 1.0 support multipart form data as well. Multi part form can have file upload data as well, It is recommended to add the file upload parameter name in the parameter exclusion list.
Info
PyCript also supports WebSocket messages. The extension can encrypt and decrypt WebSocket message payloads in the same way as HTTP requests and responses.